| Introduction | Spirit | History | Technology | Human Resource | Formation |
Analyzing attack methods
Artifact analysis
"Artifacts" are traces left behind when an incident occurs. For example, malware, tools, and logs obtained from network devices are also artifacts. At JPCERT/CC, we investigate and analyze artifacts that provide evidence of an attack to study incidents including their cause [Figure 1]. Our analysis results are used to help support incident response and also provided as technical information to be widely used by companies and organizations.
Incidents and artifact analysis
Some artifacts are commonly found in various places, while others are seen only in specific attacks. Analyzing artifacts requires accuracy and caution, and what approaches to use, how detailed an analysis should be, and so on need to be strictly decided, in light of the purpose of analysis, envisioned use of analysis results, and time and other constraints. In this effort, we need to coordinate people and technology, increase efficiency, and engage in analysis day after day. At JPCERT/CC, we have a system in place to allow us to prepare and establish an analysis environment and perform reviews at any time, so that we can respond and conduct analysis flexibly according to each artifact.
Artifact analysis is a means to link threats and incidents
When an incident occurs, various artifacts may be left behind, such as malware, logs, and attack tools. It is necessary to piece together the overall picture of the incident as accurately as possible by analyzing these artifacts as a composite whole. For example, in the analysis of malware, its functions and command&control servers can be clarified, but the infection route is rarely identified. Artifact analysis is conducted from various perspectives instead of being bound by a single piece of information, in an attempt to obtain information that will help measure the scope of impact and severity of the incident. [Figure 1]
At JPCERT/CC, we gather and analyze threat information including provided artifacts so that it can be used appropriately to respond to incidents, and we support incident response and provide information based on the analysis results.
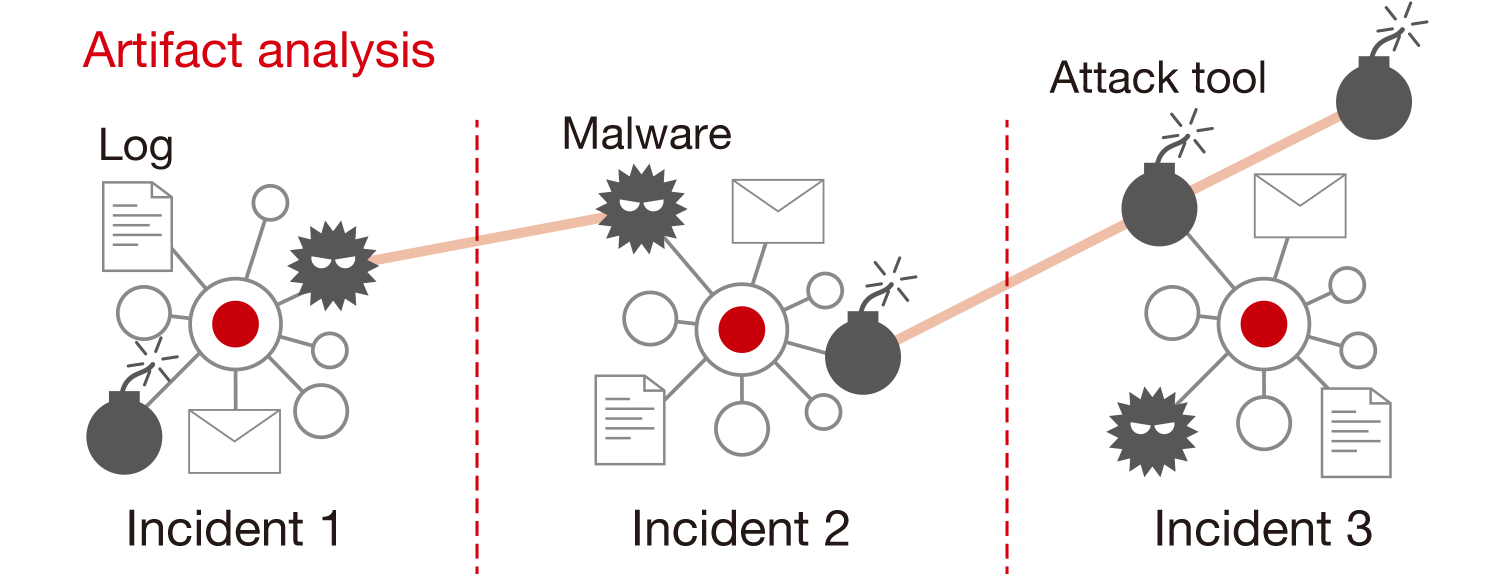
Figure 1: Identifying malware and attack tools helps reveal relationships between incidents
Providing technical information and creating a community of analyzers
To help combat growing cyber attacks, JPCERT/CC makes technical knowledge obtained from artifact analysis available to the public, either summarized in the form of reports or incorporated into tools that can be used to counter cyber attacks.
We also maintain technical interchanges through conferences with artifact analysts from around the world and other channels.
| Introduction | Spirit | History | Technology | Human Resource | Formation |

