| Introduction | Spirit | History | Technology | Human Resource | Formation |
For preventing security-related damage
Vulnerability information handling
Vulnerabilities are security weaknesses hidden in the operating systems, software, and embedded devices of smartphones, computers, home appliances, and so on. Attackers target those vulnerabilities. In vulnerability information handling, we relay information about vulnerabilities identified to product vendors to support their countermeasures, including creating patches and updates. Once the countermeasures are ready, we collaborate with the vendors to communicate countermeasure information to the product users through publication activities. This helps minimize the exploitation of vulnerabilities by the attackers and prevent the occurrence of incidents.
Delivering information about vulnerabilities and countermeasures to the right people
If vulnerability information is disseminated without any information about how to counter it, that information may be used to carry out attacks. To prevent that from happening, it is necessary to limit the sharing of vulnerability information to relevant parties until countermeasures are ready. It is also important to urge product users to quickly apply the countermeasures once they are ready.
At JPCERT/CC, we strictly manage reported information concerning vulnerabilities and delivery it to product vendors, while communicating information about countermeasures to product users in an understandable language.
Serving as a linchpin of vulnerability information in Japan and the world
In Japan, the Ministry of Economy, Trade and Industry has issued a public notice prescribing " Standards for Handling Vulnerability-related Information of Software Products and Others " which calls on those who have identified vulnerabilities and product vendors to take appropriate steps. In response to this public notice, industry groups such as JEITA, JISA, CSAJ, and JNSA, IPA[1], and JPCERT/CC have jointly established "Guidelines for Information Security Early Warning Partnership," and are conducting vulnerability handling activities based on the guidelines. In addition, JPCERT/CC also collaborates with overseas CSIRTs and researchers to disseminate vulnerability information globally.
[1] IPA: Information-technology Promotion Agency, Japan
JVN portal site as a one-stop source for vulnerability countermeasure information
Primary information about vulnerability countermeasures is released by the vendors concerned, but countermeasure information about vulnerabilities handled by JPCERT/CC is also posted on the Japan Vulnerability Notes (JVN) portal site with the cooperation of product vendors. [Figure 1]
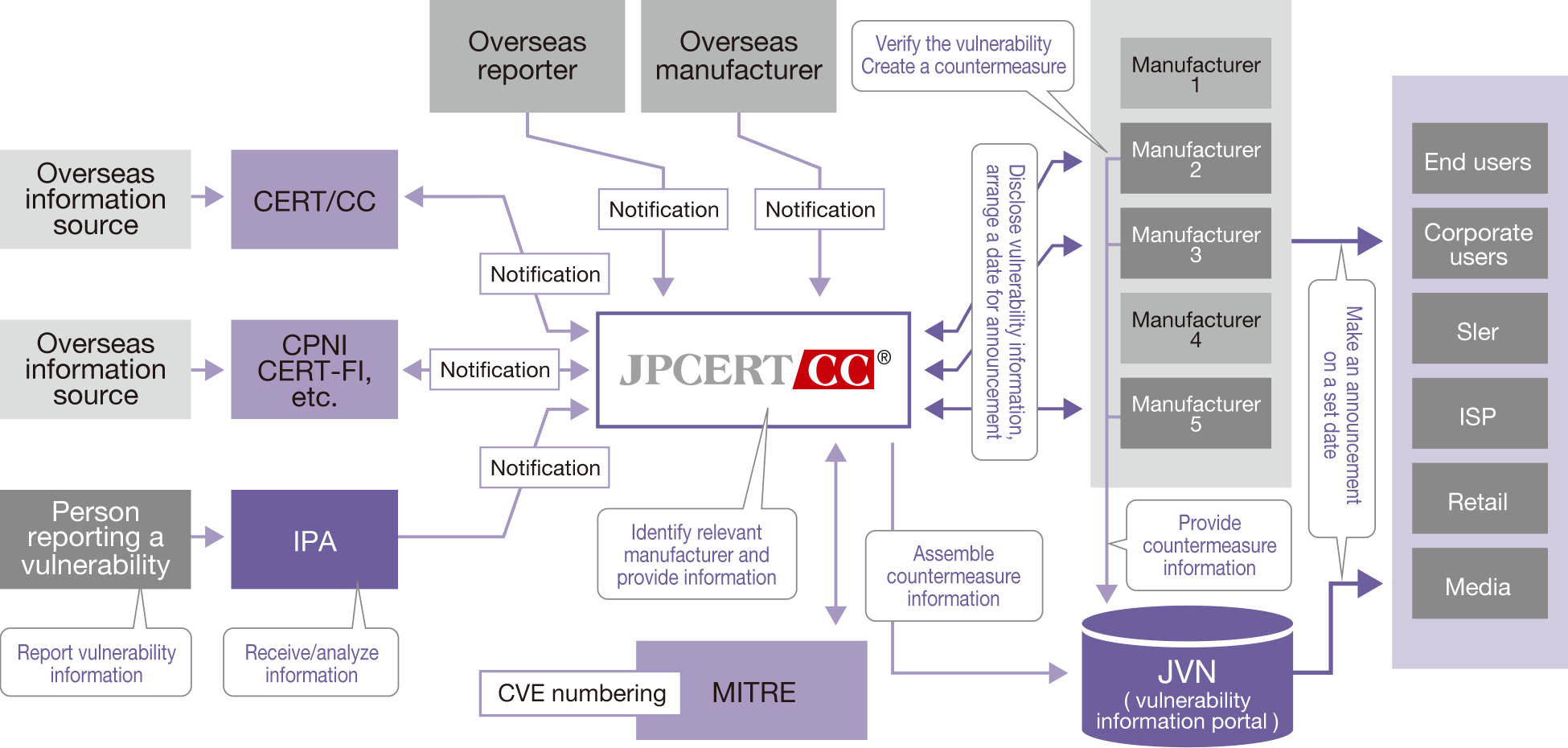
Figure 1: Vulnerability information is disseminated by JPCERT/CC and IPA and through the JVN portal site
CVE numbering: JPCERT/CC has been certified by MITRE, a U.S. company managing and operating Common Vulnerabilities and Exposures (CVE), as a CVE Numbering Authority (CNA), and assigns CVE numbers.
JVN: Japan Vulnerability Notes
This portal site provides and archives information about vulnerabilities in software and other products used in Japan, along with countermeasure information. It was launched in response to the "Rules for Handling Information Related to Vulnerabilities in Software Products, etc.," a public notice issued by the Ministry of Economy, Trade and Industry, and it has been jointly operated by JPCERT/CC and the Information-technology Promotion Agency, Japan (IPA) since July 2004. The website is intended to help system administrators, system integrators, product vendors, and others to assess the threat of a vulnerability and take appropriate countermeasures. On JVN, we provide information about vulnerabilities reported and coordinated in accordance with the Information Security Early Warning Partnership scheme, and vulnerability information coordinated with CERT/CC and other overseas coordinating bodies.
It can be used without any procedures.
Activities to promote and raise awareness of secure coding
Secure coding is gaining attention as a way to reduce vulnerabilities by taking security into consideration when developing software. This is an indispensable technique particularly in industries that provide products requiring high reliability, such as automobiles, medical devices, and control systems.
At JPCERT/CC, we create and provide various materials for learning secure coding, including a Japanese version of the "CERT C Coding Standard," which was developed at the Software Engineering Institute at Carnegie Mellon University. We also hold various seminars and events both in Japan and abroad targeting product vendors and students.
| Introduction | Spirit | History | Technology | Human Resource | Formation |

